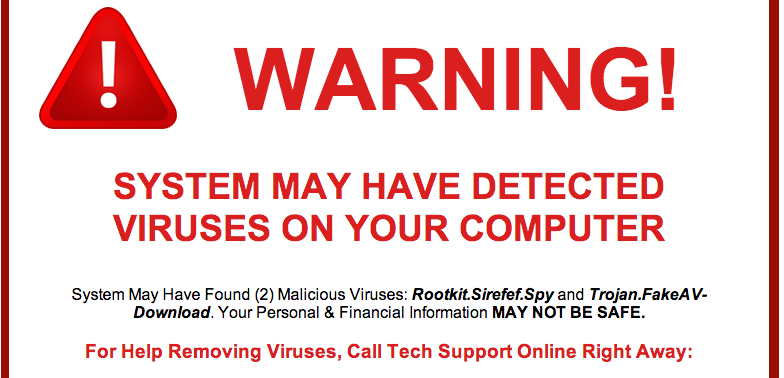
- Most scams use tech support chats or messages with an 800 number to get your attention.
- If the hacker is using the chat, they may try to convince you they need your IP address to help you diagnose and remedy your device. Giving up this information would allow the hackers full access to your computer.
-
- If you receive a pop up message requesting immediate action, remember your computers security system may ask you to update software or run a scan, it wouldn’t request your login information or that you call to speak to someone.
- If you aren’t sure if the pop up is legitimate or not call your security provider directly, use a phone number you have for them and not one that may appear in the pop up.
- If you get an unexpected phone call or text message requesting immediate action, ignore it!
- Again similar to the pop ups your provider wouldn’t be contacting you unless you initiated contact.
- Hang up if you get a call requesting immediate action, or requesting you go online and allow the tech to remotely connect to your system.
- If you receive a text message with a phone number, do not call that number.
- Again if you want to be sure your device is safe, contact your security provider directly.
If you believe you received a call that is a scam, report it!
Reports about fraudulent calls and pop-ups can be made at:
For more information and tips on safety, visit:
Microsoft – https://blogs.microsoft.com/on-the-issues/2017/05/18/fight-tech-support-scams/
Important info from this article
“Microsoft will never proactively reach out to you to provide unsolicited PC or technical support. Any communication we have with you must be initiated by you.
Do not call the number in a pop-up window on your device. Microsoft’s error and warning messages never include a phone number.
Never give control of your computer to a third party unless you can confirm that it is a legitimate representative of a computer support team with whom you are already a customer.”
–Gregoire, Courtney
Detailed information regarding Identity Theft scams and other IT security topics are available on our IT Security website at: SecureIT.Fordham.edu or from our blog at itsecurity.blog.fordham.edu
If you have any questions or concerns, please contact IT Customer Care at (718) 817-3999 or via email to: HelpIT@fordham.edu.
Original Author: Gerald Johnson Jr.