Previously, command advice for detecting phishing emails involved checking the message for grammar and spelling mistakes. With the rise of artificial intelligence and Large Language Models, traditional signs of phishing are obsolete.
How Hackers Use Artificial Intelligence
Many scammers, for whom English isn’t their first language, are now using LLMs like ChatGPT to edit out their grammatical errors. These tactics can lure users into believing phishing and scam messages are legitimate. Attackers can also use AI to find current information needed to impersonate financial institutions, the university, and its employees. For a model like ChatGPT, simply prompting it to write a phishing email isn’t possible. ChatGPT refuses, citing “ethical guidelines and privacy policy.” However, there are ways to avoid those regulations. Asking ChatGPT to write a movie script or use an alternate personality to create a phishing message are proven ways to bypass content restrictions. Fraudsters could also use “jailbroken” versions of ChatGPT, such as worm or fraudGPT, available on the dark web.
According to the Persona security blog, many fraud detection services rely on specific phrases or grammar mistakes to flag phishing, but this is no longer a viable strategy. AI can generate convincing, clearly communicated messages tailored to targeted users. Additionally, using automated web scraping, attackers can crawl over thousands of social media platforms to find contact information, use an LLM to create a spam message and deploy to thousands of users.
Artificial intelligence doesn’t just manipulate text, it can generate audio as well. AI voice impersonations are on the rise and are a terrifying tactic used for spear phishing. Scammers can use AI voice cloning to pretend to be politicians, the police, or your family members. In April of 2023, an Arizona mother received a call from who she believed to be her daughter, claiming she was kidnapped and needed a million-dollar ransom. The mother claims the audio was AI-generated to sound exactly like her daughter.
How To Detect Phishing in the Age of AI
While phishing techniques are becoming more advanced, so is the software used to combat it. Most security programs, like CrowdStrike, now use machine learning in their operations. CrowdStrike, used throughout the university, can now detect security events in real-time rather than waiting for the attack to execute and seeing if it’s legitimate. Software like CrowdStrike or ProofPoint can prevent phishing emails from being delivered in the first place. Users can also educate themselves on identifying phishy messages with the following tips.
- Check the sender’s email address and domain – When in doubt of an email’s legitimacy, check the sender’s header name and email address. Some scammers may use the name fname@f0rdham.edu or fname@fordhamedu.com instead of fname@fordham.edu.
- Look for unexpected or unsolicited messages – If an email is advertising a service you never signed up for or is from a student or faculty member you’re not in regular contact with, stay on alert and don’t click any links. If you need clarification on the validity of a message, contact the sender through alternate means before responding to the email thread.
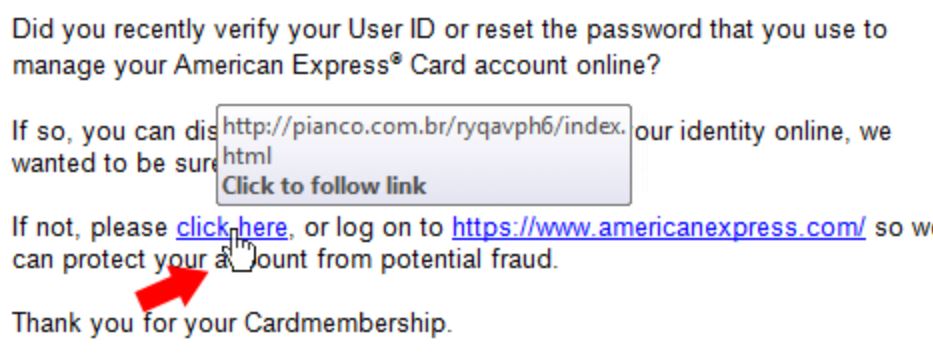
- Examine URLs – Hovering over a link (don’t click on it) allows you to see the URL and validate that it is consistent with the message content before clicking.
If you believe you’ve received a phishing email, report it to Fordham IT by contacting the help desk (HelpIT@fordham.edu), filling out a report manually on the Tech Help Portal, or using the one-click Cofense Spam Reporter for Gmail. For an in-depth tutorial on how to report potential phishing emails, visit our blog post here.
Sources:
https://www.paubox.com/news/how-to-spot-ai-phishing-attempts-and-othersecurity-threats
https://www.infosecurity-magazine.com/news/ai-phishing-emails-almost/

